Q5 Safe & Secure Step 3
CREATING A GOOD USERNAME
With over 2.7 billion people using the Internet, you will find that the username you want to use to create an account may already be taken. You will need to be creative and create a username that you will remember and be unique to you.
Work with your partner or small group, and each select one of the following resources, take notes and then share what you learned with your partners.
- 6 Things a Safe Username Should Always Do (Dashlane)
- WikiHow to Create a Unique Username (7/12/2023)
- Lifewire How to Create the Perfect Screen/Username
Note: You can check to see if your username is still available on certain sites, such as Facebook, Twitter, YouTube, Photobucket, Hulu, Bebo, and others, by using the website namechk.
MOBILE SAFETY AND SECURITY
Mobile cell phones are everywhere. They are just as important as safety and security with your digital computing device, in fact it is one of the more powerful options used today by many.
Open and Read the infographic on Cell Phone Safety (direct link here) and then discuss with a partner or in class.
- What three points from this infographic stand out to you as most important?
- Do your points align with your partners? You should each discuss why you believe your three points are the most important.
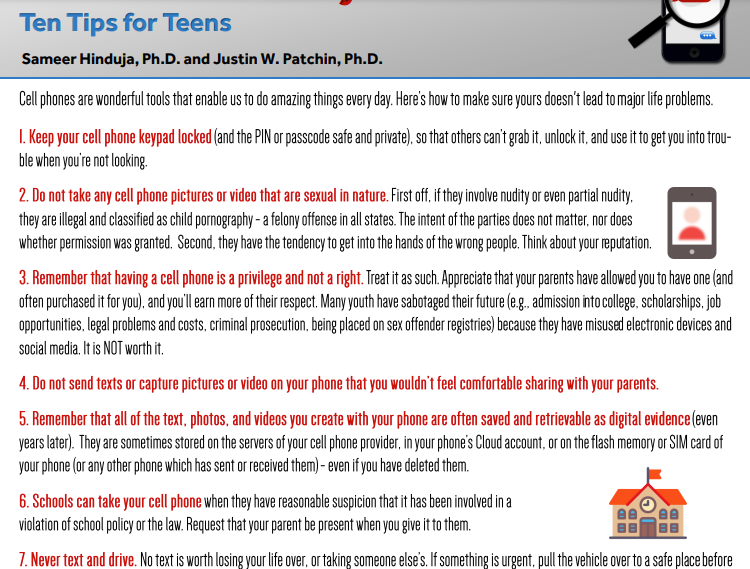
© 2018 Cyberbullying Research Center | cyberbullying.org Reproduction allowed for non-profit educational purposes only.
TWO FACTOR AUTHENTICATION (2FA)
2FA is also referred to as two-step verification. It means that you need two factors to access your account online. It could be your password AND a special code. When you set up 2FA, it will make sure that the person logging into your account is really you.
It adds a second security level (two-factors) to complete your login process to make it more secure and protect you. Direct YouTube link.
TWO FACTOR AUTHENTICATION CONTINUED
Advanced Cyber-Security Game from Nova Labs
This activity is for grades 6-12,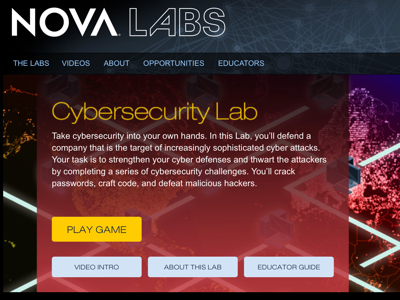 and takes approximately one and a half hours to complete. Check with your teacher about this activity located on the PBS website.
and takes approximately one and a half hours to complete. Check with your teacher about this activity located on the PBS website.
Play the Video Introduction (3:38) to learn about it.
Competencies & Standards
MITECS Michigan Integrated Technology Competencies for Students, and
3. Knowledge Constructor
a. Plan and employ effective research strategies to locate information and other resources for their intellectual or creative pursuits
Websites and Documents
Websites
- 6 Things a Safe Username Should Always Do (Dashlane)
- 8 Do's and Don'ts Of Good Passwords
- 10 Tips for Teens on Strong Passwords
- AUP Examples
- Bitwarden
- Cell Phone Safety
- How to Create the Perfect Screen/Username
- Namechk
- WikiHow to Create a Unique Username
Videos from Outside Sources
- Broken Friendship YouTube (1:50 mins)
- How to Create a Strong Password YouTube (3:30 mins)
- Two-Factor Authentication (2FA) YouTube (2:35 mins)
21t4s Videos
21t4s Documents & Quizzes




